258956
signa
https://www.finsmes.com/2024/05/blackwell-security-raises-13m-in-funding.html
signa
Finsmes
Blackwell Security, an Ann Arbor, MI-based provider of specialized cybersecurity solutions for the healthcare sector, raised $13M in funding.
The round was led by General Catalyst and Rally Ventures.
As part of the announcement, Blackwell has appointed Geyer Jones as their first Chief Executive...
The round was led by General Catalyst and Rally Ventures.
As part of the announcement, Blackwell has appointed Geyer Jones as their first Chief Executive...
258955
signa
https://hothardware.com/news/google-mandiant-virustotal-and-gemini-ai-join-forces-to-stomp-out-security-threats
signa
Hothardware
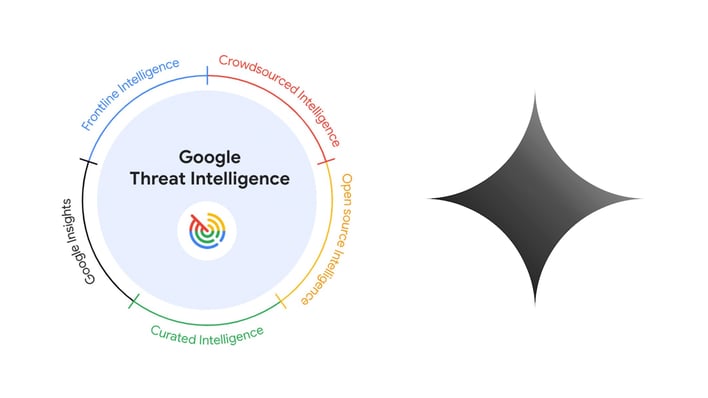
Artificial intelligence has been used for some rather interesting applications, such as helping people deal with losing a loved one. While this is a unique use of the technology, there is so much more that AI can be used to improve our daily lives. This includes cybersecurity, which Google is now capitalizing on by integrating its Gemini AI model into the new Google Threat Intelligence Platform, announced at the RSA Conference in San Fransisco.
258954
signa
https://www.finsmes.com/2024/05/token-security-raises-7m-in-seed-funding.html
signa
Finsmes
Token Security, a Tel Aviv, Israel-based machine-first identity security platform provider, emerged from stealth, announcing $7m in Seed funding.
The round was led by TLV Partners and SNR as well as a range of angel investors including Shlomo Kramer, one of the founding fathers of cybersecurity...
The round was led by TLV Partners and SNR as well as a range of angel investors including Shlomo Kramer, one of the founding fathers of cybersecurity...
258953
signa
https://www.dcvelocity.com/articles/60724-siemens-launchs-new-sinec-security-guard-saas
signa
Dcvelocità
Production facilities are increasingly the targets of cyberattacks. Industrial companies are therefore required to identify and close potential vulnerabilities in their systems. To address the need to identify cybersecurity vulnerabilities on the shop floor as quickly as possible, Siemens has launched a new cybersecurity software-as-a-service.
258952
signa
https://cfotech.co.nz/story/trend-micro-enhances-ai-security-with-new-trend-vision-one-platform-features
signa
Cfotech
Global cybersecurity firm, Trend Micro, has expanded its Trend Vision One platform with enhanced AI-powered features to secure organisational use of Artificial Intelligence (AI) and manage risks related to the increasing adoption of these AI tools. Working ahead of the upcoming RSA Conference...
TIMELINE FUTURU
PREVISIONI DI PAESE
258055
signa
https://financialpost.com/globe-newswire/blackwell-security-raises-13m-co-led-by-general-catalyst-and-rally-ventures-to-empower-healthcare-cybersecurity-operations
signa
Postu finanziariu
Stu situ web usa i cookies per persunalizà u vostru cuntenutu (inclusi l'annunzii), è ci permette di analizà u nostru trafficu. Leghjite più nantu à i cookies quì. Continuendu à aduprà u nostru situ, accunsente à i nostri Termini di serviziu è Politica di privacy.
TIMELINE FUTURU
PREVISIONI DI PAESE
258054
signa
https://www.pymnts.com/news/investment-tracker/2024/cloud-security-firm-wiz-valued-at-12-billion-after-funding-round/
signa
Pymni
Cloud security startup Wiz has reportedly been valued at $12 billion after raising $1 billion. Co-founder and CEO Assaf Rappaport discussed the funding in a Tuesday (May interview with the Wall Street Journal (WSJ), saying the company expects this year to be a time of consolidation in the cybersecurity sector.
TIMELINE FUTURU
PREVISIONI DI PAESE
258053
signa
https://rollcall.com/2024/05/07/change-healthcare-lacked-safeguards-even-as-it-gave-security-advice/
signa
Rollcall
In the months surrounding UnitedHealth Group Inc.'s $13 billion purchase of software company Change Healthcare Inc. in 2022, experts at Change published articles and policy papers extolling the need for cybersecurity measures in the health care industry.
While it dished out that advice, one of...
While it dished out that advice, one of...
TIMELINE FUTURU
PREVISIONI DI PAESE
258052
signa
https://www.siliconrepublic.com/business/akamai-noname-security-acquisition-deal-api-cloud-cybersecurity
signa
Repubblica di Silicon
Based in Massachusetts, Akamai Technologies has previously acquired Ireland's Asavie to expand its global cloud and cybersecurity business. Akamai Technologies announced today (7 May) that it has agreed to acquire Noname Security in a $450m deal to meet growing demand for API security. Headquartered in San Jose, California, Noname is a privately funded company that specialises in the API (application programming interface) security market.
TIMELINE FUTURU
PREVISIONI DI PAESE
258051
signa
https://www.techcentral.ie/microsoft-restructures-security-governance-aligning-deputy-cisos-and-engineering-teams/
signa
Tecnica centrale
Redmond adopt 'six pillars' for better detect threats. Microsoft is restructuring part of its upper management to elevate cybersecurity governance. Engineering and a group of deputy CISOs will partner to oversee SFI, manage risks and report to senior leadership, Charlie Bell, EVP, Microsoft Security, said in a blog post.
TIMELINE FUTURU
PREVISIONI DI PAESE
258050
signa
https://www.jurist.org/news/2024/05/uk-armed-forces-network-breached-in-alleged-china-cyber-attack/
signa
Ghjurista
UK Grant Shapps confirmed Tuesday that a cybersecurity incident had taken place involving the UK Armed Forces payment network, in an oral statement before the House of Commons. Shapps said the Ministry of Defence (MoD) had identified a security breach in the network that involved the leaks of data of some 272,000 UK Armed Forces personnel.
258049
signa
https://blog.qualys.com/qualys-insights/2024/05/07/qualys-is-proud-to-sign-cisas-secure-by-design-pledge
signa
Blog
Cybersecurity leaders in the U.S. are very familiar with the Cybersecurity and Infrastructure Security Agency (CISA) and their important work to keep the internet, our country, and its citizens safe from cyber threats. As part of their efforts, CISA has identified secure by design software as a...
258048
signa
https://www.hackread.com/uk-security-provider-leaks-guard-suspect-data/
signa
Hackread
Amberstone Security LTD., a prominent security provider in the United Kingdom linked to the Argenbright Group has suffered a major cybersecurity incident in which a misconfigured cloud database was found exposing 1.2 million documents with sensitive information.
The database, which spanned 245.3...
The database, which spanned 245.3...
258047
signa
https://blogs.cisco.com/security/accelerating-saas-security-certifications-to-maximize-market-access-2
signa
blog
The regulatory landscape for Software-as-a-Service (SaaS) offerings is rapidly changing worldwide as governments seek to address concerns around privacy, security, and data sovereignty. While the European Union's Cybersecurity Certification Scheme for Cloud Services (EUCS) has set a high standard...
258046
signa
https://www.cnx-software.com/2024/05/07/microchip-pic32ck-32-bit-arm-cortex-m33-mcu-combines-hardware-security-module-with-arm-trustzone-for-iot-cybersecurity-compliance/
signa
Cnx-software
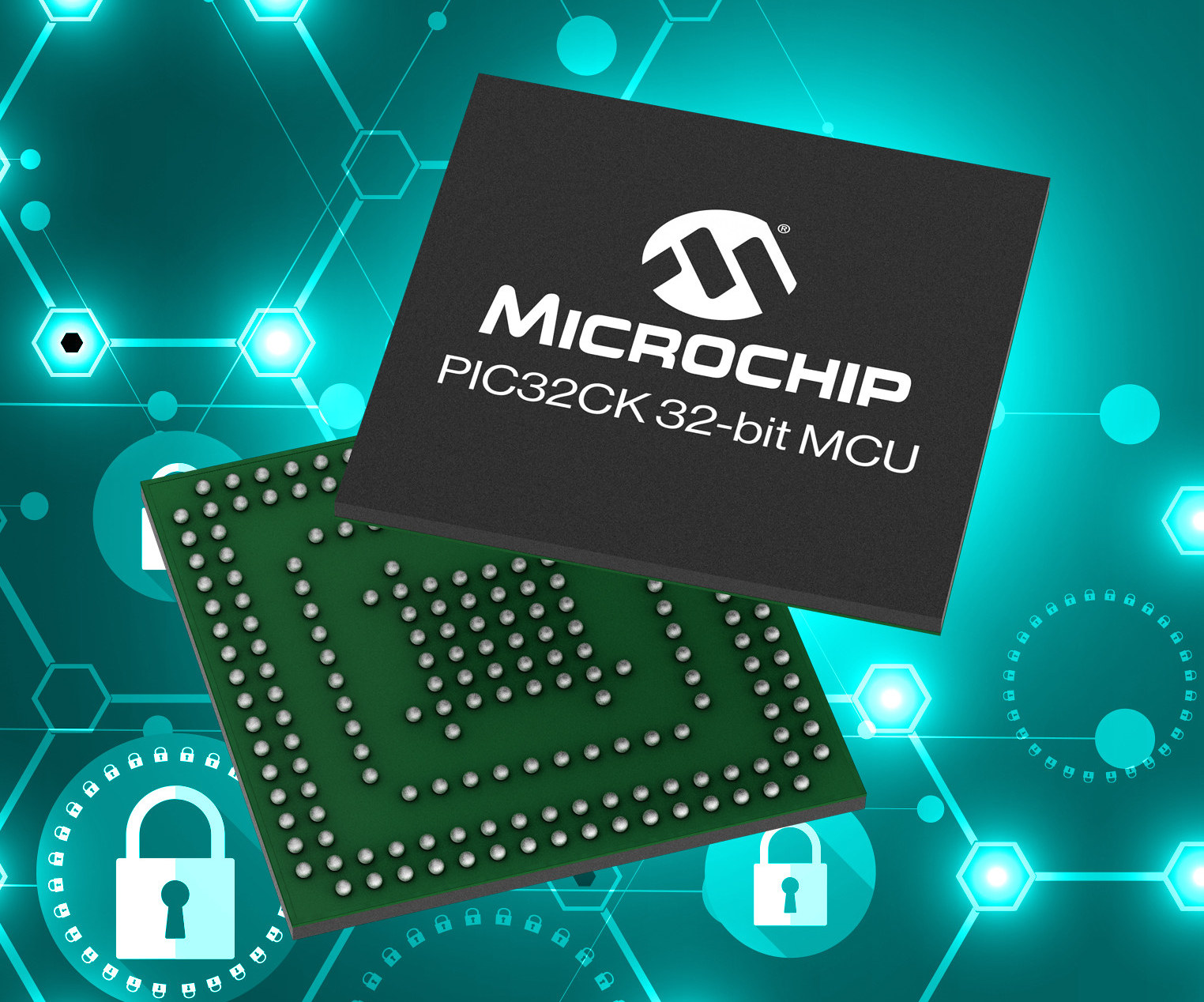
Microchip PIC32CK is a new family of 32-bit Arm Cortex-M33 microcontrollers clocked up to 120 MHz with Arm Trustzone and an optional integrated Hardware Security Module (HSM) that can help companies meet the cybersecurity requirements for consumer IoT devices and critical infrastructure mandated...
258045
signa
https://www.helpnetsecurity.com/2024/05/07/abnormal-account-takeover-protection/
signa
Helpnetsecurity
LockBit leader unmasked: US charges Russian national Ransomware operations are becoming less profitable 6 tips to implement security gamification effectively Cybercrime stats you can't ignore The strategic advantages of targeted threat intelligence.
258044
signa
https://www.helpnetsecurity.com/2024/05/07/forescout-ai/
signa
Helpnetsecurity
LockBit leader unmasked: US charges Russian national Ransomware operations are becoming less profitable 6 tips to implement security gamification effectively Cybercrime stats you can't ignore The strategic advantages of targeted threat intelligence.
257247
signa
https://www.analyticsvidhya.com/blog/2024/05/openai-security-measures/
signa
Analitica vidhya
Artificial intelligence (AI) significantly impacts various sectors today. It can potentially revolutionize areas such as healthcare, education, and cybersecurity. Recognizing AI's extensive influence, it's crucial to emphasize the security of these advanced systems. Ensuring robust security measures allows stakeholders to fully leverage the benefits AI provides.
257246
signa
https://www.cnet.com/tech/services-and-software/rsa-conference-2024/
signa
Cnet
From the hundreds of panels and talks to the often quirky expo floor displays, artificial intelligence and its potenial impact on the cybersecurity industry is the topic of choice at this year's RSA Conference in San Francisco.Tens of thousands of data security professionals, business moguls,...
257248
signa
https://blogs.nvidia.com/blog/rsa-2024-ai-cybersecurity/
signa
blog
Cybersecurity experts at the RSA Conference this week will be on the hunt for ways to secure their operations in the era of generative AI.
They'll find many of the latest tools use AI and accelerated computing. This intersection of security and AI is coming into focus with collaborations that...
They'll find many of the latest tools use AI and accelerated computing. This intersection of security and AI is coming into focus with collaborations that...
257249
signa
https://theinventory.com/crowdstrike-falcon-go-cloud-based-cybersecurity-softw-1851457726
signa
L'inventariu
Unwavering cybersecurity is no longer a luxury, but indeed a necessity given the rapidly evolving digital landscape. If your business is in search of a trustworthy, efficient, and all-inclusive solution, look no further than the CrowdStrike Falcon Go, a next-gen antivirus software available on...
257251
signa
https://www.internetsafetystatistics.com/cybersecurity-white-hat-hackers/
signa
Statistiche di sicurezza in Internet
Cybersecurity threats are a constant worry in today's digital age. But have you ever wondered who protects us from these threats? Enter white hat hackers - the ethical guardians of the internet. This series dives into the fascinating world of these cybersecurity professionals, exploring their...