260819
Îşaretên
https://www.theregister.com/2024/05/10/microsoft_president_brad_smith_summoned/
Îşaretên
qeyd bike
The US government wants to make Microsoft's vice chair and president, Brad Smith, the latest tech figurehead to field questions from a House committee on its recent cybersecurity failings. The House Committee on Homeland Security has proposed the hearing take place later this month on May 22. It will be referred to as "A Cascade of Security Failures: Assessing Microsoft Corporation's Cybersecurity Shortfalls and the Implications for Homeland Security." In recent times, Microsoft has faced a barrage of criticism following some significant revelations about its security practices.
260818
Îşaretên
https://www.brsoftech.com/blog/implementing-mobile-threat-detection/
Îşaretên
Brsoftech
As of 2023, there were about 8.6 billion active smartphones in the world. With more and more people and businesses adopting this tech, something else has also crept up from the dark: cybersecurity threats targeting mobile devices. . In November 2022 alone, there were almost 2.1 million cyber attacks primarily targeting mobile phone users.
260817
Îşaretên
https://www.verdict.co.uk/google-gemini-can-now-generate-a-cybersecurity-response-playbook/
Îşaretên
Hûkûm
Google's AI model Gemini can now be used to generate a response playbook for enterprise cybersecurity teams.
Gemini in Security Operations can now assist security teams in threat detection, as well as generating response playbooks using natural language.
Cybersecurity teams can then refine the...
Gemini in Security Operations can now assist security teams in threat detection, as well as generating response playbooks using natural language.
Cybersecurity teams can then refine the...
260816
Îşaretên
https://barrie.ctvnews.ca/tech-giant-launches-1st-canadian-global-security-operations-centre-in-barrie-1.6880829
Îşaretên
barry
The City of Barrie officially became the site of Kyndryl's first global Global Security Operations Center (SOC) in hopes of addressing the need for expanded cybersecurity infrastructure across the country.
The tech giant celebrated its opening with a ribbon cutting ceremony on Thursday...
The tech giant celebrated its opening with a ribbon cutting ceremony on Thursday...
259917
Îşaretên
https://betanews.com/2024/05/09/get-the-devsecops-playbook-deliver-continuous-security-at-speed-worth-19-for-free/
Îşaretên
Betanews
In The DevSecOps Playbook: Deliver Continuous Security at Speed, Wiley CISO and CIO Sean Mack delivers an expert analysis of how to keep your business secure, relying on the classic triad of people, process, and technology to examine -- in depth -- every component of DevSecOps. In the book, you'll learn why DevSecOps is as much about people and collaboration as it is about technology and how it impacts every part of our cybersecurity systems.
PÊŞEROJÊ TIMELINE
259916
Îşaretên
https://www.smallbiztechnology.com/archive/2024/05/tunnelvision-attack-strategy-compromises-vpn-security.html/
Îşaretên
Smallbiztechnology
The recently discovered attack strategy, TunnelVision, has caused concern among cybersecurity experts by compromising VPNs. This method influences VPNs to route a large volume of data traffic outside of their secure encrypted channels, thus endangering data privacy and security. TunnelVision...
PÊŞEROJÊ TIMELINE
259915
Îşaretên
https://www.computerweekly.com/opinion/Zero-Trust-Unravelling-the-enigma-and-charting-the-future
Îşaretên
Computerhefty
For nearly two decades, the concept of Zero Trust has perplexed and intrigued IT and cybersecurity professionals alike. It's been labelled a vulnerability, a decision, a mindset, and even a paradigm shift. Its definition is as elusive as its application is broad, underpinning a diverse array of technologies.
PÊŞEROJÊ TIMELINE
259914
Îşaretên
https://washingtontechnology.com/companies/2024/05/tech-firms-pledge-release-products-built-security-features/396455/
Îşaretên
Teknolojiya Washington
SAN FRANCISCO — Nearly 70 tech and cybersecurity companies on Wednesday signed a U.S.-led pledge to bake default security features into their offerings, a move that Biden cyber officials have been pushing for months in an effort to shore up the baseline security of off-the-shelf tech products.The...
PÊŞEROJÊ TIMELINE
259913
Îşaretên
https://blog.qualys.com/product-tech/2024/05/09/how-to-create-collaboration-and-shared-goals-with-it-and-security-teams
Îşaretên
Blog
In today's ITSM landscape, merging IT operations and security practices is no longer "ideal", but imperative. According to a recent Gartner® Board of Directors Survey 1, 88% of respondents indicated that their organization perceives cybersecurity as a business risk. This was up from 58% in 2016,...
PÊŞEROJÊ TIMELINE
258956
Îşaretên
https://www.finsmes.com/2024/05/blackwell-security-raises-13m-in-funding.html
Îşaretên
Finsmes
Blackwell Security, an Ann Arbor, MI-based provider of specialized cybersecurity solutions for the healthcare sector, raised $13M in funding.
The round was led by General Catalyst and Rally Ventures.
As part of the announcement, Blackwell has appointed Geyer Jones as their first Chief Executive...
The round was led by General Catalyst and Rally Ventures.
As part of the announcement, Blackwell has appointed Geyer Jones as their first Chief Executive...
PÊŞEROJÊ TIMELINE
258955
Îşaretên
https://hothardware.com/news/google-mandiant-virustotal-and-gemini-ai-join-forces-to-stomp-out-security-threats
Îşaretên
Hothardware
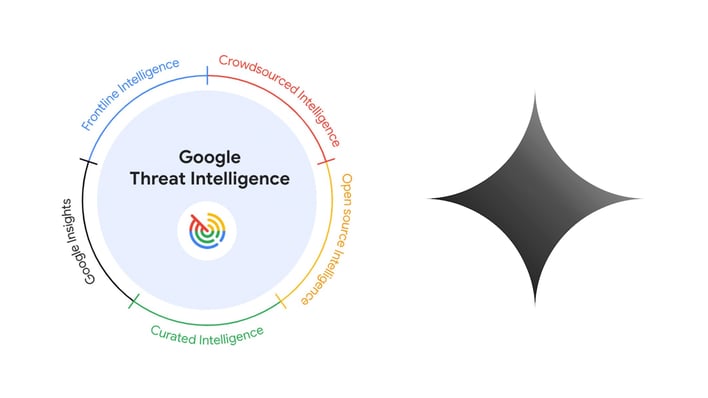
Artificial intelligence has been used for some rather interesting applications, such as helping people deal with losing a loved one. While this is a unique use of the technology, there is so much more that AI can be used to improve our daily lives. This includes cybersecurity, which Google is now capitalizing on by integrating its Gemini AI model into the new Google Threat Intelligence Platform, announced at the RSA Conference in San Fransisco.
258954
Îşaretên
https://www.finsmes.com/2024/05/token-security-raises-7m-in-seed-funding.html
Îşaretên
Finsmes
Token Security, a Tel Aviv, Israel-based machine-first identity security platform provider, emerged from stealth, announcing $7m in Seed funding.
The round was led by TLV Partners and SNR as well as a range of angel investors including Shlomo Kramer, one of the founding fathers of cybersecurity...
The round was led by TLV Partners and SNR as well as a range of angel investors including Shlomo Kramer, one of the founding fathers of cybersecurity...
258953
Îşaretên
https://www.dcvelocity.com/articles/60724-siemens-launchs-new-sinec-security-guard-saas
Îşaretên
Dcvelocity
Production facilities are increasingly the targets of cyberattacks. Industrial companies are therefore required to identify and close potential vulnerabilities in their systems. To address the need to identify cybersecurity vulnerabilities on the shop floor as quickly as possible, Siemens has launched a new cybersecurity software-as-a-service.
258952
Îşaretên
https://cfotech.co.nz/story/trend-micro-enhances-ai-security-with-new-trend-vision-one-platform-features
Îşaretên
Cfotech
Global cybersecurity firm, Trend Micro, has expanded its Trend Vision One platform with enhanced AI-powered features to secure organisational use of Artificial Intelligence (AI) and manage risks related to the increasing adoption of these AI tools. Working ahead of the upcoming RSA Conference...
258055
Îşaretên
https://financialpost.com/globe-newswire/blackwell-security-raises-13m-co-led-by-general-catalyst-and-rally-ventures-to-empower-healthcare-cybersecurity-operations
Îşaretên
Financialpost
Ev malper ji bo kesanekirina naveroka we (tevî reklaman) çerezan bikar tîne û rê dide me ku em seyrûsefera xwe analîz bikin. Zêdetir li ser cookie-yan li vir bixwînin. Bi berdewamkirina karanîna malpera me, hûn bi Mercên Karûbar û Siyaseta Nepenîtiyê razî ne.
258044
Îşaretên
https://www.helpnetsecurity.com/2024/05/07/forescout-ai/
Îşaretên
Helpnetewlekariya
LockBit leader unmasked: US charges Russian national Ransomware operations are becoming less profitable 6 tips to implement security gamification effectively Cybercrime stats you can't ignore The strategic advantages of targeted threat intelligence.
258045
Îşaretên
https://www.helpnetsecurity.com/2024/05/07/abnormal-account-takeover-protection/
Îşaretên
Helpnetewlekariya
LockBit leader unmasked: US charges Russian national Ransomware operations are becoming less profitable 6 tips to implement security gamification effectively Cybercrime stats you can't ignore The strategic advantages of targeted threat intelligence.
258046
Îşaretên
https://www.cnx-software.com/2024/05/07/microchip-pic32ck-32-bit-arm-cortex-m33-mcu-combines-hardware-security-module-with-arm-trustzone-for-iot-cybersecurity-compliance/
Îşaretên
Cnx-nermalava
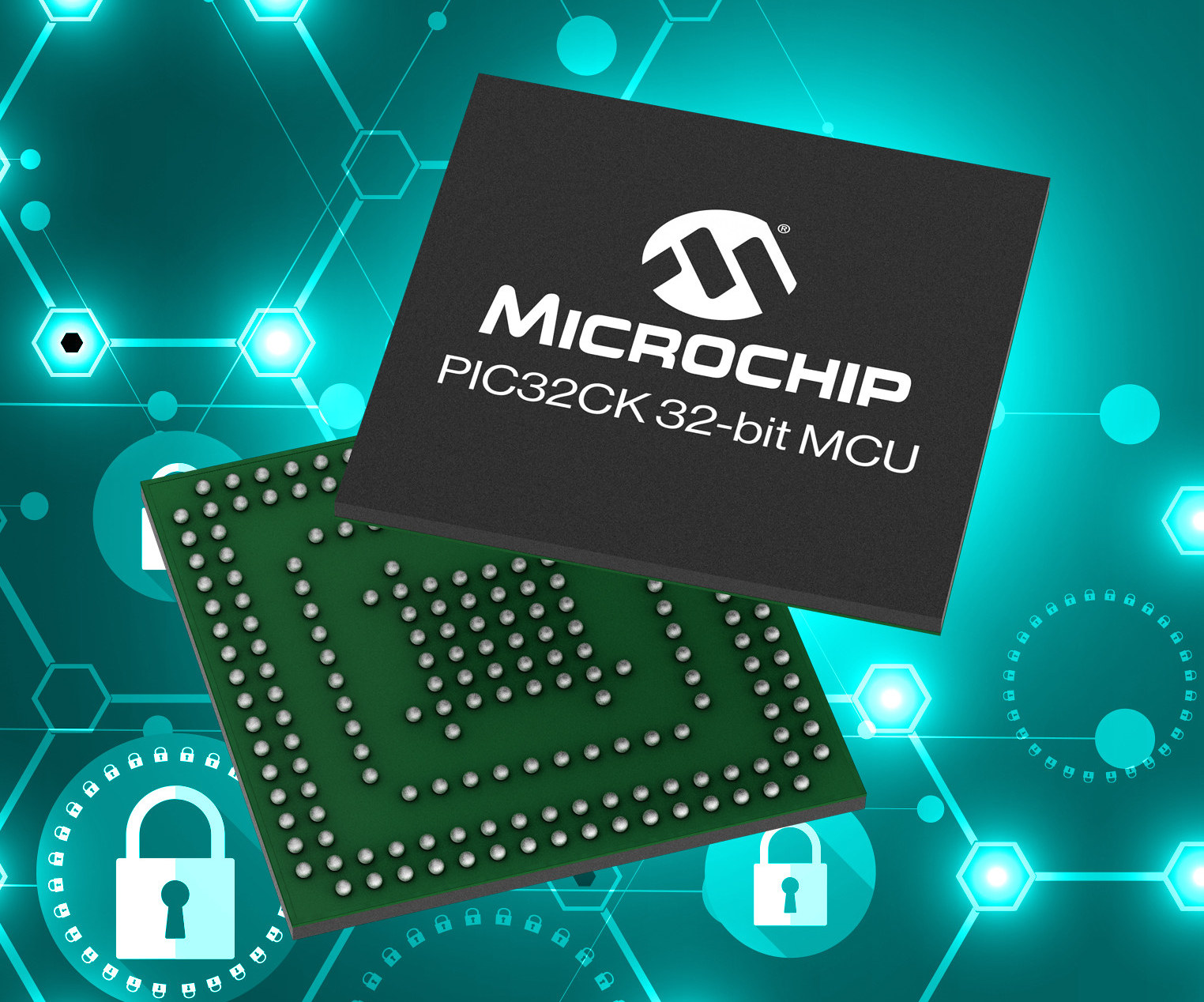
Microchip PIC32CK is a new family of 32-bit Arm Cortex-M33 microcontrollers clocked up to 120 MHz with Arm Trustzone and an optional integrated Hardware Security Module (HSM) that can help companies meet the cybersecurity requirements for consumer IoT devices and critical infrastructure mandated...
258047
Îşaretên
https://blogs.cisco.com/security/accelerating-saas-security-certifications-to-maximize-market-access-2
Îşaretên
Blogs
The regulatory landscape for Software-as-a-Service (SaaS) offerings is rapidly changing worldwide as governments seek to address concerns around privacy, security, and data sovereignty. While the European Union's Cybersecurity Certification Scheme for Cloud Services (EUCS) has set a high standard...
258048
Îşaretên
https://www.hackread.com/uk-security-provider-leaks-guard-suspect-data/
Îşaretên
Hackread
Amberstone Security LTD., a prominent security provider in the United Kingdom linked to the Argenbright Group has suffered a major cybersecurity incident in which a misconfigured cloud database was found exposing 1.2 million documents with sensitive information.
The database, which spanned 245.3...
The database, which spanned 245.3...
258049
Îşaretên
https://blog.qualys.com/qualys-insights/2024/05/07/qualys-is-proud-to-sign-cisas-secure-by-design-pledge
Îşaretên
Blog
Cybersecurity leaders in the U.S. are very familiar with the Cybersecurity and Infrastructure Security Agency (CISA) and their important work to keep the internet, our country, and its citizens safe from cyber threats. As part of their efforts, CISA has identified secure by design software as a...
258051
Îşaretên
https://www.techcentral.ie/microsoft-restructures-security-governance-aligning-deputy-cisos-and-engineering-teams/
Îşaretên
Techcentral
Redmond adopt 'six pillars' for better detect threats. Microsoft is restructuring part of its upper management to elevate cybersecurity governance. Engineering and a group of deputy CISOs will partner to oversee SFI, manage risks and report to senior leadership, Charlie Bell, EVP, Microsoft Security, said in a blog post.